OAuth2 for webhook notifications
Azupay supports OAuth 2.0 as an authorisation framework for webhooks we send to our clients. OAuth 2.0 is an authorisation framework commonly used for securing interactions between different applications or services. It has the following uses cases/benefits:
- Webhook requests can be secured through OAuth 2.0 which is a widely used security standard supported by most API gateways.
- The OAuth 2.0 standard provides regular token rotation, minimising security exposure if a token is intercepted.
- Improved security for static open PayIDs where the PayID is long-lived and requires regular webhook interaction on the same PaymentRequest over months or years.
How to implement OAuth2 webhook authorisation
To implement OAuth2 based authentication, you will need to implement an OAuth2 resource server which Azupay can authorise against via the Client Credential grant flow.
You will then provide Azupay authorization details via a secure channel that include the following fields:
Field | Decription |
|---|---|
tokenUrl | A HTTPS endpoint that the Azupay client can request OAuth2 tokens from used in the OAuth2 Client Credential flow |
oauthClientId | The clientId assigned to Azupay for OAuth2 requests |
oauthClientSecret | The clientSecret used by Azupay for Authorisation to request an Oauth2 token |
sendClientCredentialsIn | Whether you want the ClientCredentials to be sent in the header or body of the request (valued values are "header" or "body". Header is generally supported as defined in the RFC spec, but POST body is also supported to support broad compatability. If set to 'header', null, or undefined: Credentials are sent in the Authorization header (Basic base64_encoded_credentials). |
oauthScope (Optional) | The oauthScope is configured to define the scope of the OAuth2 token. This can be used if you have multiple webhook configurations that require specific webhooks to be ingested by specific endpoints that may have different security scoping |
url | The URL which webhook events should be sent to |
How do I host an OAuth2 resource server?
Azupay provides the following list of popular OAuth2 resource server hosts that can help , however we can't provide any general advice on if any of these options is appropriate for your specific use case.
These platforms can act as both an Authorization Server (AS) and host a Resource Server (RS) to validate tokens and serve protected data:
- Auth0 – Can validate client credentials tokens and expose APIs as resource servers.
- Azure AD (Microsoft Entra ID) – Supports API management via Microsoft Identity Platform, allowing resource servers to validate tokens.
- Google Cloud IAM – With Google API Gateway or Cloud Endpoints, you can enforce token validation.
- Okta – Can act as both an identity provider and enforce OAuth2 security on hosted APIs.
- Apigee (Google) – Provides full API management with OAuth2 token validation.
- IBM API Connect – Includes built-in OAuth2 authorization and resource hosting.
- Kong API Gateway – Can enforce OAuth2 authentication for APIs acting as a resource server.
- AWS API Gateway (via Cognito or IAM) – Can validate OAuth2 tokens against Cognito or IAM.
Resources
- OAuth2 RFP Client Credential Grant documentation (https://datatracker.ietf.org/doc/html/rfc6749#section-4.4)
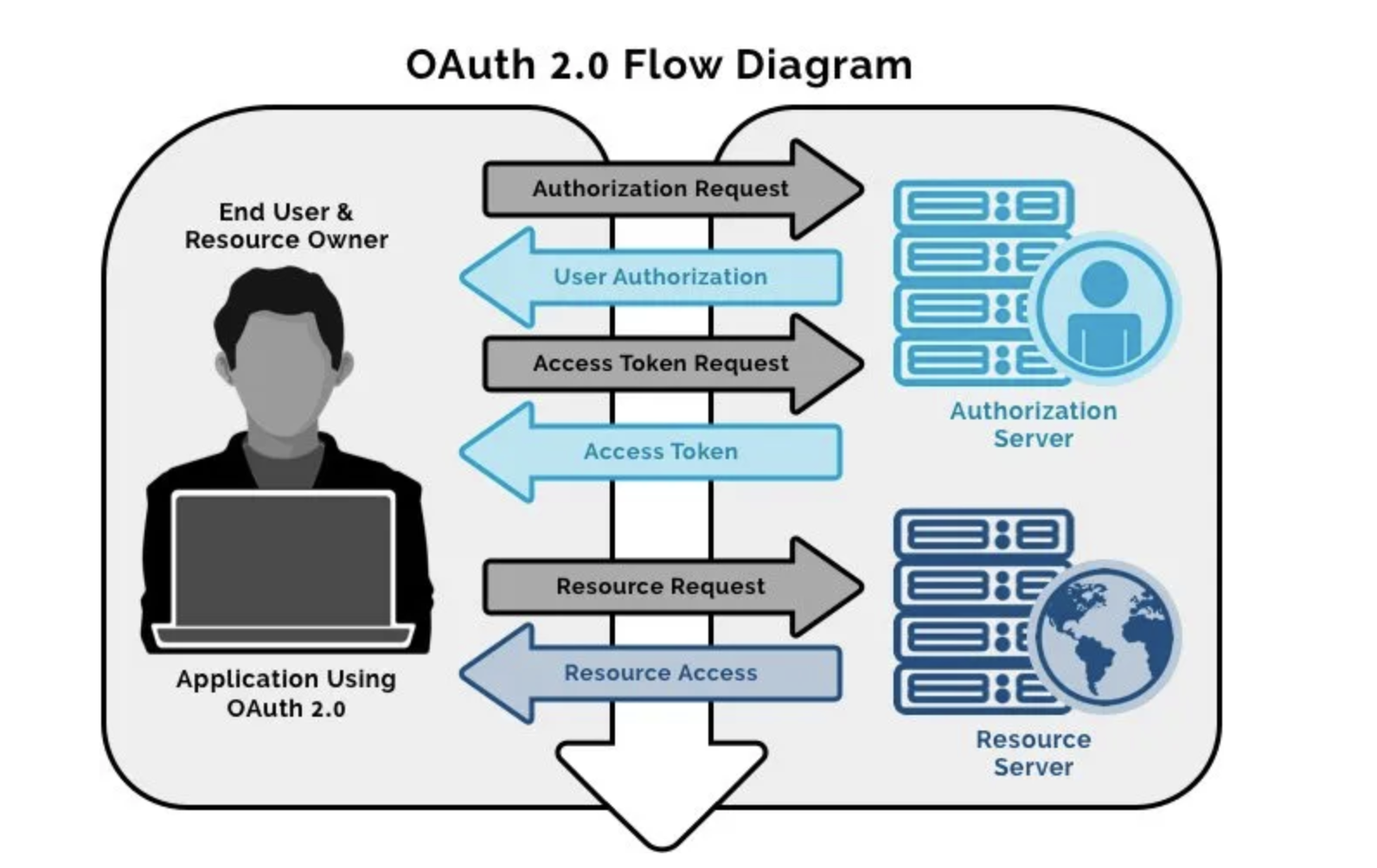
OAuth2 High Level flow diagram
Updated 3 months ago
